00:02
Hello and welcome to this month's coffee break. It is July 20th depending on what time zone you're coming to us from escaping ransomware, jail protection before during and after attack. My name is Andrew Miller. I'm your host every month joined today by Andy Stone and I see each other a good bit, Andy. Thank you for being here today. A little bit of housekeeping to start off as always.
00:21
Not too much. Hey, it's a coffee break. It's an official thing. We've got a cool logo that goes to it. We've actually, we're now into month. I want to say 19. Thanks to the solution focus. A lot of these have aged better than average would encourage you to look back at these. There's even a bit link there.
00:35
You can find this online or in the follow up email that will be sent out. And if you're thinking about this topic today, actually focusing on ransomware attack and we've hit on recovery and disaster cover business, continuity and ransomware. All these pieces that kind of orbit around this topic for joining us today. Thank you for doing so. Um You should be seeing by no later than
00:54
tomorrow, a $10 Starbucks gift card in your email. This is only for folks who attend. I hope you think, you know why II I think you know why as well as there are certain folks where you you may not receive this because of what we're allowed to send you next month. This is a series.
01:10
So next month we're gonna go a little bit different. Each month is a little different. We gonna have John Owings on he was actually on about a year ago with Michael when we talk about all things Cober, Netti and Port works. We're actually going to spend the first half talking about kind of John's career arc starting in networking,
01:25
even Citrix and VM Ware and storage and how he's based wandered away from hardware over the course of his career. But he still works here at pure, doing a lot of really neat stuff in that in that theme. And then the second half will dive into a bunch of updates around the Kubernetes port works, port works, data services landscape. And this is stuff that John focuses on in his
01:42
current role here as well. OK. Actually, yeah, there we go. I didn't mean to pause the music for a second. We'll pull down in a second as well. One other fun event, we usually try not to do too much cross promotion here because we want to keep the focus on the solution focused. But I think a clean cover band is kind of
02:00
different enough, but it's interesting to put up. So we've got an event running on August 18th, uh Justin Emerson who's uh phenomenally sharp going through uncomplicated your data storage with flash blade and then uh ultimate clean tribute band, not actually clean, the surprise, you know, kind of thing. And if you missed Accelerate,
02:18
there is still, you can register for the online sessions. And if you are actually in, depending on the city that you're in, there are a number of accelerate road shows. I'll be actually at the ones in Oklahoma City and Tulsa next month. Just go to the website, you can find them. Please join us if you, you missed Accelerate or
02:33
you want more of it. You want to hang out with pure folks with their, you know, pure customers, et cetera with that. I'm Andrew Miller, your host. As always, I'm not going to introduce myself fully. But as it relates to this topic, Ransomware specifically for better or worse,
02:48
I've been talking about it now for the last five or six years, Andrew Miller Ransomware into Google, you'll find stuff. But even because I started with, you know, a pair of Cisco picks 5 25 firewalls and there was proxy filters. Anyone remembers Nobel border manager, even some endpoint protection.
03:04
I've got friends that are CIS SPS. I'm not one of them, but, you know, I try to be aware of security landscape over the years because if you're going to be a good architect, you actually need to understand how things break intentionally or maliciously that feels like good architecture relates pretty quickly into security stuff. You've got joining me today, someone who comes from a little bit of a non-traditional
03:23
background as far as pure goes, Andy. Do you mind introducing yourself? Yeah. Hey, everybody. I'm Andy Stone. I'm the CTO for the America Pure Storage. And um I come with a broad set of backgrounds really uh 25 years in the information security space. I've held a number of roles from consulting to
03:42
being AC O uh to, you know, leading all of it for large organization, Pricewaterhouse Coopers as the US and Global CTO. And so, um, yeah, lots of security I would say in my background. Very cool. Uh One thing I, I appreciate and we, we've talked about this is that I'm, I'm real about my background,
04:00
you know, partner, customer for a while, partner for a while, you know, technical marketing, doing stuff up here. I, I can't say the, I've been AC O, I've been a CTO just like, and so what I appreciate is when, when, when you and I tag team events because if folks haven't figured out Andy and I, we were together at accelerate and otherwise we can
04:15
come at it with a line perspective, but different perspectives too, you know, kind of thing, which is a lot of fun. So diving into this month, escaping ransomware, ransomware, jail protection before during and after an attack. As always a little bit of an agenda. Not too much. And like it says, um this is a painful
04:34
challenging topic industrywide. So we're gonna do our best. No ambulance chasing here, right, kind of thing. But we're gonna talk about real stuff that challenges four sections, first evolving life cycle of a ransomware attack, then thinking about defense in depth areas of security event, life cycle focus then as always in the kind of the second half,
04:53
we're gonna wander into areas that pure can help here. It's more than we can cram into the time. So we're not gonna cram it and we're gonna, you know, spend a full half talking about a larger landscape. And then actually, I know near and dear to Earhart Andy is the idea of resiliency and resiliency architectures.
05:08
Maybe that's another way to say defense in depth. But, but I like the word resiliency in this case before we dive into the first one. Emily. Do you mind putting up the first poll? We're trying to do this as a little bit of a um, a regular thing. Maybe even a palette cleanser. It keeps you all engaged.
05:21
I mean, hopefully it's interesting for you to see what all of your peers out there are thinking. We've got close to 1000 folks on it is three questions this time. Each of these will be three questions they're hopefully, uh, relatively easily. Um, Andy, I think we promised that all this is, this is all anonymous, right. So, so if you're feeling a little queasy and,
05:41
and if, if, of course, if, like, you'd rather not say that that's totally fine too. Um, so has your organization experienced a ransomware attack? You know? Yes. One time, maybe more than once. How long did it take to recover? Maybe you're in just the, don't ask, you know, that's a little humorous, but sometimes it's like we just don't want to
05:56
talk about it. Like, um, if we want to go to the incanto, you know. No, don't talk about Bruno. I don't talk about ransomware recovery time. So I won't. Do you want to do the song Bruno song, Andy or should I, or neither of us? Maybe you, you can do it.
06:10
Ok? Or maybe neither of us. And then, um, you have to do a dance with it though. Oh, ok. I'll, maybe we'll do that at the end of the Q and A I, I'll bring that up. How much data would you expect to regain access to if your organization paid a ransom?
06:25
So I'm actually gonna let this keep ticking for a second. Um Just because I, I want to give people time to answer. We're about, you know, 300 folks here. But Andy, so we'll leave the pull up. I don't think Emily obscures the screen. So let's think about the life cycle of ransomware attack.
06:41
Often this is from a, before, during and after frame cheating. I know that's how you like to usually talk about it. Andy, do you mind kind of start walking through what that life cycle looks like? Yeah. Sure, Andrew. So, you know, on the before side I, I think there's a lot to kind of understand and unpack
06:58
even before we get to, you know, the ransomware piece and that, that really starts with the Attackers themselves. You know, what we're generally finding is that the Attackers from a ransomware perspective anymore are not that sophisticated, technologically. A lot of them are going out, they're going to the dark web.
07:15
They're gonna rent the ransomware as a service as a platform uh from a provider for about 100 and 49 bucks a month. And for that, they're gonna get all the tools that they need to actually exploit an environment. So they're gonna get everything that they need to basically launch that ransomware attack and even to go further to actually collect payment
07:34
on the back end. So they usually, when they rent the platform also have a split with the, the the platform provider. Uh it's usually like a, a 40 60 you know, 30 70 sort of split that goes in favor of the attacker, we'll say and for that, they get negotiation services and Bitcoin collection services. So, you know, when, when you do get attacked,
07:56
in essence, it's the platform provider that you're negotiating with, they collect the ransom and then they'll distribute it to the attacker downstream. But these Attackers are mostly business people. They're going out and figuring out who they should attack, who's likely to pay, uh you know, so that they can in essence get their Bitcoin and move on. Now, along similar lines, they're not even the
08:17
ones necessarily launching these watering hole campaigns or fishing attacks to get credentials into an environment. Most of the time nowadays, they're going out and buying them from an initial access broker on the dark web for pennies on the dollar. So, you know, a lot that can be said in terms of the business side. Now, in terms of before an attack,
08:34
once the Attackers have this intelligence, they've decided who they're going to attack, they've bought their credentials or, or acquired their credentials, they're gonna log in to your environment basically as a regular user. And, you know, then they're gonna use the tool that they've rented to basically elevate their privilege in the environment.
08:52
Now that time between login and elevate is called breakout time in security terms. So used to measure that in hours. Now it's down to about 90 minutes. So what that means is you have about 90 minutes from the time a bad guy gets into your environment with regular credentials to the point that they elevate to administrator and are able to move kind of laterally across the environment.
09:11
Now, that's important to understand because it really will play into some of what we talk about, you know, and how you can protect yourselves later on when the, the ransomware gets deployed in the environment. A lot of times modern ransomware runs in memory. Um You know, it's basically doing a few things in the background.
09:29
It's watching how users are interacting with files, um you know, unstructured data and as a user goes to save a file, uh and the device, so let's say you're working in powerpoint and you go to save it, the ransomware payload is gonna pick up on a couple of things and it's going to actually make a copy of that file and it's gonna pre encrypt it.
09:49
So it, it does that by skipping a 1st 512 bytes of the file, which is the header, it'll encrypt up to the next meg and it's gonna skip anything bigger than that. And then it's gonna store it in a, in a hidden directory called the volume shadow store. Um And then it's gonna put a good copy of the file where the user expected it.
10:06
So that way when the attacker decides it's time to launch their attack, the call from a command and control server in the cloud, it'll then delete the files in the good directory, move the files from the, the hidden directory into that their place. And it looks like this really high speed encryption campaign is going on. So, you know,
10:24
a lot that's happening there pre the actual attack. So the reason ransomware is so hard to detect is because it's running in memory and you'd have to literally be able to take memory snapshots of all your running devices, do comparisons to known bad signatures before the malware mutates and identify, you know, the ransomware as a running process, which is just nearly impossible.
10:49
There's also been the scenario seems to have just done, you know, the Attackers targeting credentials, you know, to like an actor directory, domain admin level. And then if they can do that and potentially put key loggers around, how do you detect if someone is actually their credentials have been uh vaulted somewhere else and stored somewhere else to use during the attack,
11:05
it's a legitimate storage admin, you know, so that's right. And, and you know, once you get admin domain admin, especially you use a lot of these devices are using integrated authentication. So what that means is once you have admin on one device, you can move pretty freely to other devices with those admin credentials. Now. So storage platforms, the bad guys know what
11:25
they all look like. They know Dell they know netapp, they know pure, they know everybody, right? And so when they get in and they elevate that privilege, they have pretty much free will to go in and delete files, same thing with the backup environments, you know, they know all of those as well. They know your cohesive con vault, you know, rubric everybody and they're gonna attack those
11:44
too. So just know that before an attack, there's a lot going on in terms of intelligence, they're also gonna be looking for files that they could potentially exfiltrate from your environment to use as a secondary attack vector. We see a whole lot of that going on. But, you know, keep that in mind that there's a lot that, that, you know,
12:00
goes into building the attack, I think during and after I was beyond, beyond and actually, maybe I'll take a, take a quick pause here and if that's all right, so I want to give folks some extra time on the pole and then we'll jump back to the life cycle here. So I'm gonna end this here and we'll share back the results and even kind of comment a little bit.
12:17
Let me share the results on the screen here. I think everyone can see them now. Hopefully. So, uh to me, this is always just kind of interesting. So for folks here, um kudos to the 39% of you that haven't experienced an attack. We're definitely at a uh majority, you know, 52 at one time or more than once.
12:33
I'm gonna guess what the rather not say is to be honest, you know, just being, being real um recovery times, the less than a day is awesome. But man, there's a lot of week in a month in there or that don't ask. And then of course, um the expectation about recovering if you pay a ransom, anything that you wanna, you wanna highlight there any before I,
12:53
before I close this on the poll. I mean, I think, you know, kind of what I would expect to see in terms of who's been hit. It's just a matter of when not, if so just keep that in mind, you need to be prepared for these events. Um, you know, we're seeing a lot more destructive events that take place.
13:09
Uh, there have been a num a couple of companies, you know, in the last couple of months that have, have said they've gone out of business because of ransomware attacks. So, you know, I think that's an interesting ploy but, um, you know, the other thing that I think is interesting is in terms of regaining your files,
13:24
um, that's probably pretty accurate, you know, because the bad guys don't want to sell you a bad key. Like they're not generally in intentionally giving you a bad key. The reality though is these guys don't necessarily test that their decrypted all that. Well, the process. Yeah. So, so what you find is that you,
13:42
you end up with like, uh what we had at, at colonial where, you know, they buy the decrypt but it's single threaded. So it means it's gonna be crypt, a single file at a time. So if you have billions of files that you need to get back, it's gonna take a really, really long time.
13:58
So, I think, uh, from a, during and after you're hitting on dwell time and exfiltration, actually, for those who are running, we are going to go into how to protect anything else you want to highlight here from a kind of a life cycle standpoint. Yeah, I mean, I think, you know, for the most part we've covered, I think all of that just know that your backups are gonna be targeted,
14:16
your primary storage is gonna be targeted, data will likely be exfil. So you know that along with the fact that that these Attackers will likely plant other indicators of compromise in your environment. So back doors, if you will and those can serve as secondary or tertiary attacks because a lot of times they'll get sold on the dark web as well. So just know that that it's not necessarily
14:37
just the ransomware campaign, there are lots of other pieces that are likely to unfold as well. And, and one just this is just being very real. I mean, the last point that you have there is talking about exfiltration, that's there's some tools out there and this is all defense and depth, lots of stone landscape, but that's really hard to protect against or I I don't want to give
14:55
anyone false hope that there's great foolproof ways to protect against exfiltration. But it's, it's a threat that's hard to deal with. Well, the ransomware too, like anybody that shows up to you, you and says, hey, we can detect ransomware attacks before they actually occur. They're lying right turn and run the other way as fast as you can because they're,
15:13
they're selling snake oil at this point. So, it, you know, it's a hard problem. Sorry, I wasn't trying to cut you off. I thought, I thought, I thought it was an so Emily, do you mind launching the second poll here? And we may leave this up for a little bit longer too.
15:25
There's a great question if we're gonna go into ways to help. Yes, that is literally the next section. So poll number two. Uh Do you have a logging platform in place? We'll talk about the matters. Are you logging everything? Hopefully the answer is yes. And how concerned are you that your data protection methods could be beaten up by
15:42
ransomware attacks. We're gonna tell some, some stories there in a minute. So into part number two, as always to keep it moving. So defense in depth areas of security event life cycle focus. I'm pretty sure you like to use the same before during and after there.
15:56
Andy. So do you mind continuing? No, it's great, you know, before, during and after is, is a good theme. So, you know, before an attack, the number one thing that, that you need to be aware of and focused on is hygiene bar. None. Right. Where you can keep your system up to date and
16:09
patched, you would make it way harder for these Attackers to get into your environment initially and to elevate privilege, right? And where they encounter resistance, as we said, they're, they're not technical gurus, these are not people coming up with zero day attacks in most cases. So where they encounter that resistance, they're a lot more likely to just turn and go
16:27
the other way, hit the easier targets, right? So where you make yourself a harder target, they're likely you're, you're likely to probably deter an attacker and send them somewhere else, they wanna get paid. Is this a little bit of, you don't have to run faster than the bear, you just have to run faster than your friend or, or is that getting too dark now? No, I, I think that's accurate,
16:47
right. So, I mean, just, you know, don't, you don't want to be the slowest kid on the playground for sure. So just make sure that you're doing the hygiene and by good hygiene, what I recommend, you know, and look, these are some lofty goals, but this is what you should be aspiring to be able to patch a critical vulnerability in a day,
17:01
a high within a couple of days, mediums within a week and lows within a month, right? That should be your, your in-state target, right? For a really, really solid. Um patch management program. Now, the next thing to focus on is authentication, authentication is important for two fact,
17:17
two reasons. One is Multifactor authentication, which is is great, but it's not insurmountable and you can get around Multifactor authentication. It's not that hard, right? But what I really tend to focus on here is admin credential vaulting. So where you vault your administrative credentials in your environment,
17:35
you make it really, really hard for these Attackers, right? Because they can't elevate their privilege easily to, to move laterally. So credential vaulting is something like uh a psychotic or a beyond trust or um a a cyber arc where you actually have to check out the administrative credentials to use them.
17:53
So you, you check them out as an administrator, you use them for the task that you need to perform when you're done, they get checked back in when that happens, the passwords get rotated. So no person ever knows what that password really is. So again, makes it really hard for an attacker. But the catch here is you have to vault all of your admin credentials.
18:12
You can't just pick and choose some of them, right? Because if you do that, you're still gonna leave yourself fully exposed. So it's really hard, it's expensive. But where you do it, you make yourself a much harder target. Now, the next thing I talk about a lot of times is education,
18:27
education in two forms, awareness training for your end users, right? So fish me campaigns or something along those lines. So don't click these bad links, that kind of thing. Um But the important thing with those is you really have to know how to measure the outcomes, the out inputs of those trainings.
18:43
So it's not just a matter of running them and seeing how you did, you need to have a way of tracking the users that need remedial attention, know your users and your environment who are consistently gonna click the bad thing or open the bad thing, right? So that you can go to them and you can give them additional training.
18:59
The second piece to education is tabletop exercises, working with your, your executive staff to basically run them through end to end how one of these scenarios would unfold. And it's really important that you do this at least once a year with the executive team, if not twice and once every couple of years with the board, if not every year.
19:18
Now, I know Andrew likes to talk a little bit about the um you know, our, our table top that we recently ran. So you, you want to add any color here? Yeah. What's fascinating that even pure storage. So I, I was an observer for peer tabletop exercise being real. I shouldn't be doing hands on it. Probably not.
19:34
I mean, I have in the past and I still think I know what I'm doing. But so, so I was an observer when we had 2030 folks in it and then 23 folks who observers, what's fascinating is even as pure storage, so much of the tabletop exercise was not act about the recovery process about ransom or about encryption. It was all about who gets notified. When how are things communicated externally if
19:52
possibly someone that looks like an employee puts out a tweet externally about an attack, what was it actually the employee or a fake account or did their account get compromised? Like there's all this stuff that orbits around and that's the value of a tabletop exercise because there's a lot of core technology pieces that have to be there. If we don't, if we don't have data to recover from, we've got a big problem.
20:10
But then there's all this other stuff that wraps around it. That's the value of a tabletop exercise. And the last piece that, that I'll cover is logging, right? And, and I'll come back to this in a couple of minutes with Andrew as an area that pure can help. But the important thing to understand about
20:24
logging is you need to log everything, log all of your systems and ingest those logs into a big warm and hot pool of data. And it has to be on a fast backend platform because you have to be able to correlate events at the same time you're ingesting data. So that requires a lot of speed. You need to correlate events across three areas, the network,
20:46
the endpoint and the end user, all three. So network endpoint and end user. And the idea is you're looking for anomalies and basically a needle in a haystack. So you're collecting all this data, you're looking across network endpoint and user looking for any anomalous behavior. And you need to orchestrate those outputs to your cyber threat hunters by doing that. You're basically,
21:07
instead of saying, go search the field over there for a needle in a hay, you know, the needle that might exist, you're giving them a sniper scope and you're saying, go look right there for the needle. And so you're making their jobs way more effective. Now, why is that important? It all goes back to that 90 minutes of breakout time, right?
21:24
So the faster you can ingest and correlate events, the more likely you are to be able to find those Attackers before they can break out in your environment and launch an attack. I think with that, if it's all right, Andy, I'm gonna close the poll down and we'll riff there and then keep going here. So thank you everyone for participating. I left it up for a little while. Just so I had folks time to read.
21:43
This is anonymous. I saw some questions. So logging platform in place. Wonderful. It makes me happy. You know what? We're not here to be like bearers of doom where we don't want the answers to be good. We want them to be good, logging everything. Uh, I, I'm gonna toss one story in there.
21:57
Uh, 11 large organization, I'm familiar with the first indication they had of an attack was when an account executive, someone in a sales role logged into an active directory. Domain controller. There's no world in which that should happen even though I've worked with some great account execs over the years. Right, kind of thing. They shouldn't be logging into an ad domain
22:13
controller. And then how concerned? Uh Thank you. Thank you Emily for sharing. Uh How concerned are you, uh that your data protection methods could be corrupted? Um And this is fascinating, you know, that put those together very and somewhat concerned. That's 85% good for you. That's something that you should be concerned
22:32
about. We'll keep parking on that as we go along the way, I think, Andy back to you for, uh, for kind of during and after I'll just build this out here. So you can kind of these all interrelate together. So I'm not trying to constrain you just, you know, keep going. Yeah. Yeah. Yeah.
22:43
Um And you know, the, the other, the last point on logging is you gotta log everything. So just like vaulting all of your admin credentials, you need to log all your systems. Otherwise you have blind spots, you can't defend what you can't see. So keep that in mind now during an attack what do, what do you focus on, focus on containment? Right?
23:00
How do you quickly lock down the environment and you need to do that using virtual networking rules in a lot of cases. So segment out those devices that might be affected. You can even physically isolate devices if you need to on the network by literally going and pulling a network cable. A as a last line of resort.
23:18
What you don't ever do though is shut a system down, never turn the power off to a system that's been attacked. When you do that, you lose most if not all of the forensic capability. So you know, make sure you leave the systems running, isolate them on the network as however you need to, but don't turn the power off this. The last thing here mobilizing your incident
23:39
response team. So both internal and external so that they can be there to help you start the recovery right away. Now, after the attack, one thing that matters and that's it. Then executives don't care about your backup solution. They don't care about your storage, any of that, right?
23:55
Care about. One thing is the business back up and running yet. If not, why not? And when will it be? Right. So that's the focus is speed. How fast can I get recovered. So we're focusing on rapidly restoring the data using snapshots if you can, if they, if you have them available,
24:13
that's always the fastest way to get back up and running a backup service should be your last line of defense. Frankly, you wanna have it, you want to back up your data, you know, to, to a good backup solution. But that's your last line of defense for recovery because it's always gonna be slower than snapshots or anything ahead of it. Architecturally, communication is absolutely
24:34
key. Making sure that people stay aware, make sure that you've invoked the right support channels. So external legal counsel, external uh incident response, et cetera. Um and, and you know, start your recovery as fast as you possibly can. You know, I toss three things in there. One. It, it was fascinating one,
24:51
customer chatting with that, they were literally following the attacker from machine to machine as they were trying to take their environment off the internet. Uh I've heard the statistic, I don't think I can. This is an official one but I, I think it's Microsoft corporate not Azure can actually get off the internet within like 12 to 15 minutes, you know,
25:06
internationally, which is actually pretty crazy to think about how would you cut down all those connections while you still maintain access? So Attackers can't be doing stuff. Number two, the point about recovery and about works as an offline environment there. Um One of the most common questions I get is, you know, do I need to restore all the way back to when the Attackers got in beginning that the dwell
25:22
time gestation period you were talking about. Hm, we want to restore it right before the point of the, at the encryption phase of the attack. And then, you know, in an offline environment, clean out root gets malware. I mean, we can't roll any business back 369 months just that it doesn't work that way. Businesses go out of business.
25:38
And then the final one is about the communication piece, just especially if you're a public company. If you communicate too much, there's risk from a stock price standpoint, too little, there's regulatory risk. I mean, this is the value of that tabletop exercise, not your executives figuring it out in the
25:52
moment of what, how, what and how much should we say? That's not when you want to be figuring this stuff out. I know it's not what you wanted when you were a CTO. Well, well, not too that, you know, you always start your recovery from the point closest to the attack, possible. So if you have snapshots in place and you had a
26:06
snapshot, that was one second before an event, that's where you would start your recovery if it was an hour before a day before, you know, whatever increment before you start as close to the attack possible. You don't try to guess that, you know, six months ago, we didn't see we weren't being encrypted. So, you know,
26:22
there was no ransomware. Well, no, you, you don't, it doesn't work that way, start your recovery in an isolated environment as close to the attack as you can so that you can get up and running very quickly. Your forensics team should come in. They'll do a quick review. Um And you know, basically remove any glaring indicators of compromise while longer term
26:41
forensic review is being done in the background. Now, you need to know that when this happens, you're not likely to be able to use your existing infrastructure in a lot of cases. Somebody is gonna probably take some of your servers, your some of your storage kit, right? They're gonna want to use it for, for that forensic review process. It might be your internal team,
27:01
it might be an external team. It could be federal investigators or regulators, it could be your insurers, but no, you need line of sight to having equipment that you could potentially recover to when one of these bad events occurs with that. Emily. Do you mind putting out poll number three? And uh we'll leave this up here for a second and kind of preview.
27:23
So hygiene program in place actually chose to have this question here just because in case you weren't familiar wanted Andy to walk through some of that first for everybody as long as the discussion about, about patching critical vulnerabilities, hopefully, that's an obvious one but felt better to ask us afterwards as well as if you didn't know what a tabletop exercises hopefully you're listening.
27:40
You do now, right? Kind of thing. It's critical. We'll leave this up here again for a little while. So for the folks who said you missed the poll, uh please put it in. We will be doing Q and A at the end. So please don't hesitate to put stuff into the Q and A.
27:51
We're gonna move into sections three and four, which will kind of merge together a little bit. So thinking about the life cycle and attack defense in depth. Now, one of the things that I actually enjoy sometimes here, Pier is that I can be uh a little bit concurring with folks. It's like, hey, you don't do anything to help here.
28:05
Why? Yes, we do. There's something we can do here that and maybe more than you would expect. So, you know, say what pure can pure can help here. Obviously, we're running a whole webinar. That's why Andy's here. That's why I do a lot of this stuff too.
28:16
So continuing with that same before, during and after. Do you mind kind of starting to walk through Andy how the, the key areas that pure helps and we're not gonna cover all of it for everyone listening. We'll hit the highlights at least. Yeah, and you look, you can always follow up with us and, and we'll give you,
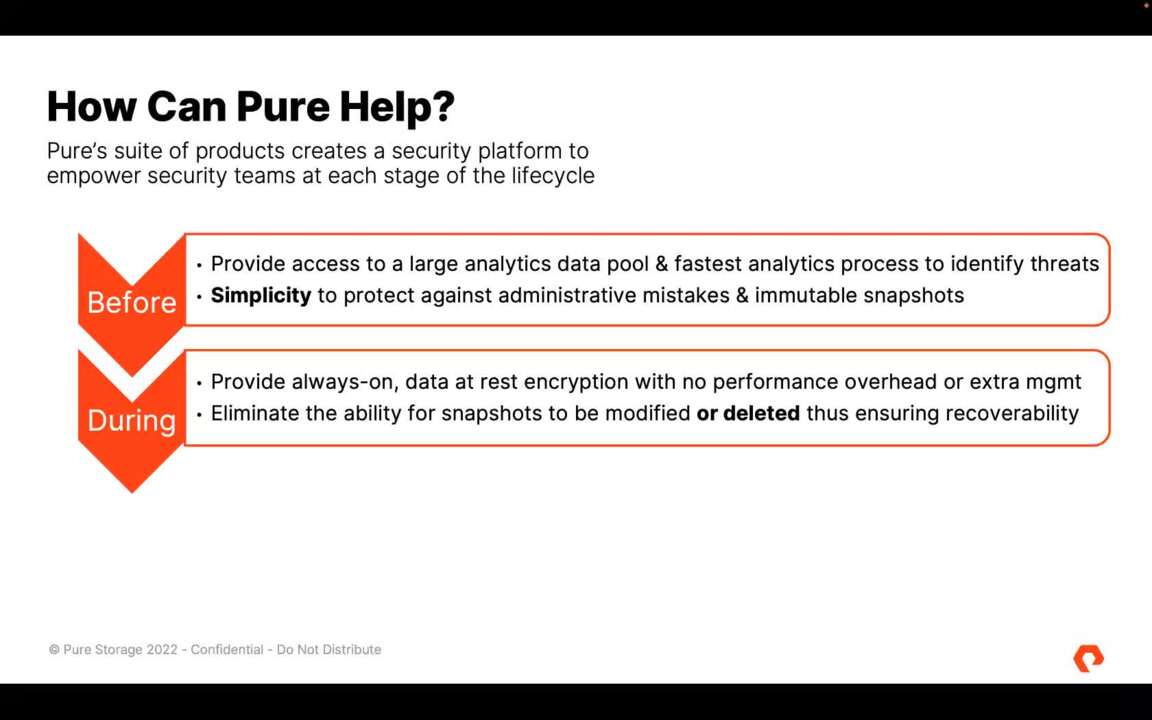
28:31
you know, we can talk through any of these points, not even just the pure ones, right? So if you want to get into more depth. So before an attack, the number one way pure can help is in that logging space, right? So again, you need to ingest logs from everything. You need those logs to be into a big hot and
28:48
warm pool of data because you need to be able to analyze it very quickly to identify those anomalies, those needles in a haystack that might exist so that you can then feed the cyber threat hunters, the the the people on your security team that are going out and looking for these bad guys actively. And so what happens is, you know, it, if your storage is too slow on the back end,
29:12
you basically get bottlenecked between ingest and correlate, right? You can't do both at the same time with slow storage. So pure, pure, we have the fastest security analytics platform back end available in the market with our flash array and flash blade security platforms.
29:29
So we allow you to both ingest and correlate at the same time, very, very fast will allow you to even put uh A A GP U in front of the storage. If you're wanting to use a very high speed compute to do some of those correlations and get full performance out of it without bottlenecking. So, you know, at pure, we're helping you build the infrastructure associated with your
29:53
analytics environment so that you have a fighting chance against the finding these bad guys before they break out and launch an attack in your environment. Remember 90 minutes is your key window. So where you're trying to correlate across the network, the endpoint and the end user, you have about 90 minutes to do that. Sometimes if you have a slow storage back end a slow analytics platform,
30:15
your queries for doing that correlation can take hours or, or days. So make sure you're running on a fast back end like Pure Andrew. Did you want to add something there? No, I was, I I think it's actually where you're going but just the the that time to correlation and then as well, just the simplicity of the platforms that's both on the underlying stuff
30:37
for analytics. It's other pieces of it takes too much time to keep the lights on a day to day basis. You're adding stuff that adds all this operational overhead. It's not gonna be there when you need it. So keep going. I'm stealing your thunder. No, I mean, that's great. And so, you know,
30:48
during an attack, the number one way pure can help is with a feature that we built called safe mode. So we built safe mode a couple of years ago. Uh for primarily insider threat protection. We had a very large customer, a hyper scalar that came to us and said, hey, pure, we're really worried that if we have a, an admin who has a bad day in our
31:07
environment, they could come in, they could delete all of our primary data, they could delete all of our snapshots and we're gonna have to go to backup to restore and that's gonna take a really long time and they are literally sl a uh by hours of downtime, right? So an hour of downtime can cost millions of dollars. So we built this feature called safe mode and
31:26
safe mode for the security folks that might be out there as a set of multifactor au out of band multifactor authenticated snapshots. Now, what that means for nonsecurity people is this, you can have some number of named administrators in your environment who have a unique pin number registered with pure support. If you need to fully delete data from a pure storage array,
31:47
two of those named individuals have to call the support, we validate them via the pin, we validate them with the account team. So we get on a zoom session live with these people and say, you know, yeah, they're still good people and then they can open a an RDP session from the customer side with pure support and support can remote in and actually help delete data that needs to be deleted.
32:07
Now, what this means is that no administrator on his or her own or even together could go in and fully delete data from a pure storage array, you have to invoke support. So a really, really unique feature, we're the only ones on the market that have this, you know, feature this capability and it basically serves as a safety net on all of your storage arrays where you're running pure.
32:30
It means that that an attacker or a bad process also can't go in and fully delete the data from a pure array. So we give you a guaranteed point of recovery right there on the array to start from when one of the attacks occurs. And again, remember you want to start from as close to the attack as you possibly can and that would be the fastest way.
32:51
So safe mode again is like the airbags on the car. It's not the only security control you're gonna use, you're still gonna use seatbelts, like in a car, you're still gonna use brakes, but the airbags might just make it so you can walk away from run one of these really bad events unscathed. So if you're a pure customer out there today, you need to make sure you're using safe mode.
33:12
If you take nothing else away from this whole, this whole broadcast, if you're a pure customer, go turn safe mode on right now because it might just save your business. It's really important. I love where you're telling some of the origin story. It's just almost this elegantly simple layer. We've had immutable snapshots for a long time
33:30
forever. Can't, that just means you can't modify it. But safe mode covers the attack vector of someone having administrative credentials, heaven forbid and actually destroying the methods of data protection, whether it's backup data stored on pure primary snapshot, data stored on pure. So it's this extra layer of resiliency if you will.
33:47
Right kind of thing that that pushes further. And it's built on top of us having on on flash ray and flash blade, a two step data deletion process for a long time, it's not worm. So it has the operational flexibility. If you have something go crazy space wise, you can actually be able to handle that to work with peer support and clean that up sooner than the data would normally age off.
34:05
We sometimes don't go any deeper than this in a totally public forum because hey, anybody can listen to this. If you want a deep dive on safe, more of the interaction there, please don't hesitate to reach out to your pure folks. Yeah, we're happy to do that. Now, the one other thing you know that I I'm glad Andrew brought up is a mutability and I'll cover that before I hit the after,
34:22
you know, again, just to reinforce everybody has immutable snapshots. That's there's nothing, you know, when other vendors talk about immutability, there's nothing secret or special about that, right? Immutability as Andrew said just means that once the data is written, it can't be changed. What it doesn't mean is that once the data is
34:38
written, it can't be deleted, right? You can go in with administrative credentials and delete immutable snapshots, safe mode is immutable plus or super immutable, right? It makes it so not only can the data not be changed, it also can't be deleted. Super important point. Now, after an attack, we already said that speed is the only thing that matters,
34:57
right? So how do you get speed? Well, with pure on the flash blade security platform, we've actually built some of the fastest integrations with backup providers on the market today. We actually have the fastest, both with cohesive and combat are partners. So, you know, with those partners, we're getting uh with cohesive petabytes of
35:16
recoverable a day with combat 270 plus terabytes per hour of recoverable and that's certified their number not ours. So you know, these platforms, the Flash Blade security platform gives you great scalability and great ability and speed of recovery, the fastest out there. Now, by comparison for those that may not know most of your storage platforms,
35:39
your traditional backup platforms are gonna give you somewhere between like two and six terabytes per hour of restore, right? So when you get into like 270 or the petabytes a day, you're talking about tens or hundreds of times faster. So keep that in mind, I mean, it's really important because every second of downtime costs, right? And where you have to touch back up,
36:00
you want that speed of recoverable. So make sure that you're focused there. Now, also after an attack going back to the logging where you chose to run your analytics, your logs on pure. You can also protect those logs with safe mode. And what that means is you now have a forensics point to go back to that you can refer back to, to look for the attacks because one of the
36:23
things that Attackers will do, one of the last things an attacker will do when they launch their attack is they'll go in and corrupt or delete logs. And by doing that, it makes the forensic process really hard. You don't know exactly what they did in the environment. Well, when safe mode is enabled, you now have a way to actually protect those logs.
36:41
So your forensics teams can go in and very quickly identify what was happening, how and where and why and they can give you faster recovery as well. Now, the last piece on this, the legal side, when you get attacked, you're gonna get sued. Somebody's gonna sue you to be shareholders, stakeholders feds. Who who knows? Right.
37:00
Somebody's gonna sue you. So where you're able to have those logs protected, you can use them to defend yourself as well because your cio ceo somebody's gonna be on the stand and an attorney is gonna say, what were you actually doing to protect this data in your environment? And they're gonna say, oh, we're doing all these great things and the next question will likely be something along
37:18
the lines of, oh, that sounds great. Prove it. And if you have to say, oh, I'd love to, but all my logs were deleted. You might as well start writing checks, right? So, this gives you a defensible way to prove what was being done in the environment as well. I'm thinking of, uh, you're having a bad day. How could it get been hit by ransomware?
37:35
How could it get worse? Here's the lawsuit. That's how it could actually get worse. You kind of think of the, uh, I'm having a bad day song from, uh Daniel Bedingfield back in the day. Uh, one or two things I want to highlight if you don't mind. Andy is just the, the idea that we can help protect primary data in place a recovery from
37:50
snapshot. Like you said, snapshots of metadata, well, architected snapshots with good metadata, there's nothing faster than that, but maybe not all the data is on pure arrays yet. So we can help protect and speed up your backup systems or maybe we've got as we should with business impact analysis, we've got multiple tiers of recovery and how we stack rank based
38:06
on the cost of downtime for that, all that kind of stuff slots in here. And I think I'm gonna go ahead and end this one last thing on this. Andrew on the, on the backup side that I failed to mention was, you know, when you start looking at backup providers, you know, you may not want to protect all of your backup data with safe mode,
38:22
but it's really important that where you are running, uh you know, these backup services protect at least the catalog services with safe. The reason is because the Attackers a lot of times will target the catalog servers because by doing that by ransoming your catalog servers for your backup environment, you render the backups useless. Right?
38:41
So that's a way less costly operation for an attacker to go ransom your backup catalogs versus having to go delete or actually ransom all of your backups themselves. Thank you for everyone who answered the poll sharing it here and then we'll go in a little bit of turbo mode for the last section here. I think we'll get to end at about the 45 minutes after the hour mark and the new Q and A. But, you know,
39:01
hang with us for a couple of extra minutes to make sure we get through resiliency. Thanks for answering the poll questions. Do you have a hygiene program in place? Majority said? Yes, great. How long does it take to patch critical vulnerabilities? It's interesting the majority there, you know, a, a majority minority,
39:16
41% at several days. And, and just so, you know, there's about a 5, 600 folks that answer this. So it's kind of a neat cross set to see. And then has your organization done a ransomware tabletop exercise with your executive team, the the majority, actually 50% just barely majority uh said yes,
39:32
which is, which is excellent. And I really appreciate the commentary from Scott as well in the chat where he's highlighting which I didn't, we didn't call out, I think as much as we could. Um snapshots can take extra space but safe mode as a feature we don't charge for this. It's a, it's built into pure systems. It fits with our evergreen uh It,
39:50
it, it, it from, from an evergreen standpoint, it fits with features being included on the array. So it's the last point, last section here, resiliency for the win. We've talked about defense in depth in one way, but there's also this idea of kind of a a tiered protection architecture. Do you mind kind of walking through that Andy?
40:09
And I'll see if I can follow the slide of animations as you're doing it. Yeah, sure. So you know, really what we talk about is a, a three, sometimes four tier sort of architecture. The first tier is all about your primary data. So where you're a pure customer and I'm gonna talk in terms of pure because that, that's what we're we we know here.
40:25
Uh you know, you're where you're running on say flash array from pure, you now can protect your flash array data with snapshots and you can have different what we call protection groups assigned on a flash array. So it's not protecting all or nothing on an array. You actually can define different policies for different volumes or applications that sit on
40:47
an array. So by doing that, you want to enable a snapshot policy and then you want to protect that snapshot policy with safe mode. Now, from you, uh what I generally tell folks is you want to keep those snapshots, those safe mode snapshots for like 3 to 7 days on the primary array. You don't want to use up a ton of space there. It's not worth it,
41:05
it will say, but right behind it, you wanna have a secondary tier, generally comprised of something that looks like flash array C or flash blade. And you want to replicate those snapshots or offload them from the primary arrays to that middle tier. And in that middle tier, you want to keep those snapshots for as long as you can afford literally.
41:24
So if you can keep them six months or a year, whatever you can afford to keep is what you should keep there. And you wanna use those for longer term forensics. One of the concepts we didn't talk about necessarily is time all times the time from which an an attacker gets into the environment. They're sitting, they're, they're launching other indicators of compromise and they're
41:43
laying in wait, they might be exfil trating data slowly. They're doing other identifying systems generally that is measured at about 40 days right now. So that means an attacker is in your environment for about 40 days. Sometimes it could be longer, sometimes it could be less, but that's a good average.
42:00
So you wanna have at least that amount of time in that middle tier so that your forensics team can go back in time for that period to look and see what might have changed. So you want to have the mid tier to save replicas of those snapshots for a long time. Go ahead, Andrew and to be clear, this could be replicated snapshots. This could also be a fast recovery tier within your backup infrastructure to accomplish some
42:23
of the same things. That's why sometimes I have to explain it like local snapshot backwards. Well, it could actually, there's multiple approaches here and this is, by the way is not, you must do this whole thing, these are options and layers along the way of possibilities, not you have to do this whole thing. So keep going.
42:36
That's right now also in that middle tier, like if you're using a flash ray C, you could use that in a pinch to run a workload that was running on flash array. So we talked about, you know, somebody's gonna come in, take your primary flash array for whatever reason, you could use the flash ray C in a pinch to run, you know, in a scaled down mode in your environment.
42:55
So you know, there are other purposes that can be served and you can work with with your pure account team, uh your, your sales engineers or, or call me or Andrew, you know, to talk through kind of what that might look like. Now, the third piece behind the mid tier is ultimately your backup, right? So backup becomes critically important.
43:14
That's where you're, you're ultimately storing, you know, your long term retention. So tier three backup. So where you have a workload that you don't necessarily want a snapshot on the front end, you do wanna still protect it with a backup, right? It's gonna be slower to recover than a snapshot. I mean snapshots we can recover in milliseconds,
43:32
you know, backup is gonna take time. But you know, it's, you still want it to be very fast where you have it and where you need it. Now, the other concept that we talk about is a tertiary site. So it could be a AD R side, a backup side, I call it a bunker sometimes. But the idea is, you know, this is a warehouse, it's kind of a one way in you replicate your
43:53
data to that that site. So you can use something like active cluster or active dr from here or you can even do snapshot replication to an uh another target, right from your primary arrays, this site becomes a primary site that that can or a tertiary site that could be used in the event of something really bad happening. So probably not a cyberattack necessarily probably more so like a fire burns down a
44:20
facility or a tornado rips through or you know, something really, really critical happens. This gives you an ability to have your data located in a safe place and you could then move the compute to that data. So, so you know good examples like if you're in an equinox, you could use metal to build the compute environment on demand as you need to
44:38
and have your data prestaged so that you get up and running really fast. There's two things I often like to highlight here is one periodically folks will say like, hey, you know, you, you have to do all of this and I kind of hit on that a little bit earlier. You could start literally if you're a pure customer turn on safe mode on your primary array. This is where we're adding layers to frankly,
44:59
this shouldn't be super super new from an architecture standpoint. You're probably doing production, you're probably doing dr you're doing back, we can layer protections on top of that. And then if you want to go all the way now this is point number two, you've been hearing lots about air gap or vaulting.
45:13
Mm Let's be real. There's no tom cruise mission impossible style dangling from the ceiling, you know, physical air gaps and enterprise. It, it's more of a logical virtual air gap. You wrote a whole blog post on the zany. It's a network draw bridge that goes down, it goes up. So if you want to take that approach, we can facilitate that with,
45:29
with pure capabilities. But we also very real about what does an air gap give approach give with usually a huge amount of complexity and redundant architecture and operational overhead versus what we can derive from a safe mode cost too. I mean, look safe mode is a virtual air gap on array, right? You don't have to duplicate the infrastructure.
45:49
You don't have all the cost of putting in the network rules. You don't have to keep it up to date, all that stuff like it just works, right? That's the important thing I think with that we're at the home stretch here, Andy or we're past the home stretch, but we're going to do Q and A and in the drawing in just a second.
46:05
So stay around with us. Thanks so much for being a great guest. I was pretty sure you would be because we've done this a couple of times. A any, any closing thoughts you want to toss in before we do uh the drawing and, and go to Q and A, my, my only closing thoughts are, you know, one, please engage us to talk about the resiliency architecture like we're happy to
46:22
talk about it even not in the context of pure, right? But let's talk about, you know how to build the right architectural resiliency. Let's talk about how to build the right, security protections in your environment. The second is where you're a pure customer. Please go make sure you have safe mode turned on. There's nothing worse than doing an event like
46:41
this and getting a call tomorrow or a slack tomorrow morning saying, oh, such and such customer was hit by a ransomware attack overnight. You know, and now they're asking you to turn safe mode on. Well, guess what safe mode is not a time machine. It doesn't go back in time to get your data back after an attack.
46:56
You have to have it turned on. So, you know, make sure you're using us in that way. So I'm guessing some folks let's be real. You might have stayed around for the drawing, hopefully stayed around for the good content. We kept interesting back and forth in the polling, the drawing for the ember mug. This is the cool one that you can control with
47:15
your phone because of course, we need to do that to keep our beverages hot. It's actually kind of, I've seen some cool testimonials about people who actually get real value out of this. It's not just, just even a gimmick. It's actually pretty. Um, the one that I got, it's actually sitting on my wife's desk because she loves tea and she drinks a lot more tea
47:27
than I do. The winner is Steve L from Ohio. Steve. Hopefully you're here. Emily will be reaching out to you. Um Thanks for staying with us as well. Um To wrap up, please make sure to join us next month for the hardware free zone at a from network VM ware
47:44
storage Kubernetes and then we'll end in with all things that pure has been doing in this space, updating around that. But we are actually now formally done. It's uh 49 after the hour depending on where you are, but always like to actually stay around. We kind of, we kind of let our hair down hair's not long enough to really do that.
48:00
But, you know, it's a little bit more relaxed. Folks have been putting some stuff in the Q and A which I really appreciate. So we kind of put the music up here a little bit. Uh I don't think Andy, you and I were too stodgy, you know, at all. But, you know, it's even a little more relaxed. Now, I think I'm gonna pull that Q and A panel over here because there were some great
48:19
questions. Um, then I'm going to start with, I think I will start with, um Lee and I'll, I'll, I'll just follow these back and forth. So, so Lee asked, have we heard, have you heard about ransomware reversal software, uh capital Rs on that? If so, what are your thoughts about just being real? I haven't heard about that category.
48:41
Andy, I'm, I'm putting you on the spot, you know how well, but is that the one you heard of. Um, yes, vaguely. And I look, the reality is, you know, you could go back in time with a, a Zer or something along those lines, right. But, you know, the idea is you want the ability
48:58
to recover all points of your environment, what I'll say, and this is kind of gonna feed back to one of Gloria's early questions too is, you know, you, you want to create a recovery environment that is defined by application needs. So you need to work with your application owners to understand how quickly they need and expect to get data back when an event occurs.
49:19
Not all applications are created equally and there are some dependencies that are absolutely required before you can get some applications up and running. So for instance, active directory, dns and time services, I call those tier zero applications, right? If any of those gets hit, you're completely down, right? So where you can run those, I'm pure,
49:38
you should because you can use safe mode to protect them to get back up and running really fast, right? But those tier zero applications are absolutely critical to protect, but you're gonna have dependencies in the chain. So you need to understand from your application owners which applications are the most critical, which are 2nd, 3rd, 4th and so on so that you can set the right expectations for recovery
50:00
time objectives. I'm gonna take a couple here and kind of put them together and I'll run with an answer on this and then there's always in you can, you can join into. So a question about a plan for safe mode per volume, safe mode, working with snapshot based backup programs as, as well as um as well as the raw capacity for
50:19
safe mode, snapshots. So safe mode per volume, we've recently introduced with flash array 6.3 software, uh the ability to do what we call per um per object safe mode where in this case, the object is actually a protection group. So safe mode doesn't have to be a ray wide. It can actually be at a more granular level. That actually part of the reason for introducing that was in some cases,
50:41
people need more granular in general. I actually want my preference is for you to start with having a ray wide safe mode. That way you don't figure out what you needed to protect when it's too late, you know, kind of thing. But the one of the very specific reasons we introduced that more higher level granularity is around backup programs. We're partnered with com vat beam cohesive
50:57
others that actually trigger maybe kind of ephemeral snapshots or managing snapshots inside their catalog so that we can actually work with that better. So please don't hesitate to Jason and George to reach out to your account teams. We're happy to walk through that more deeply. We've done a lot of work specifically with the combat and beam there.
51:14
And the question about the percent of capacity that safe mode snapshots consume. So I want to make sure it's clear they're snapshots. Those are based on the change of data after de Dulic application and compression on flash array after compression on flash blade and safe mode just pre prevents actually removing those snapshots faster than you should otherwise.
51:33
Uh So it, it's about the malicious deletion scenario. Um So we can actually do things where we help look at your change rate and model that out. Really good questions, anything you want to tack on there. And because I kind of um I I use with customers and there's 20% right? So if you don't have snapshots enabled today on your arrays and your array is like say 50% you
51:54
don't expect it's 20% overhead to enable snapshots. So that'll take you to 60% utilization, right? But with, with snapshots enabled, there is no additional overhead for safe mode, right? So safe mode is literally a check box. It doesn't cost you more storage with all pure snapshots, there's no performance overhead.
52:14
We use metadata pointers to to create snapshots and store them. So there's no overhead from a performance perspective associated with our snapshots. They're instantaneous. One other practical one is there reference architecture for flash blade s and Splunk. Yet to be honest, I'm not sure. But the cool thing is thing that we previously
52:34
had with flash blade the classic flash blade, if you will flashlight classic actually applies to Splunk just the same from an overall integration standpoint. So Andy mentioned it's coming but there's some other things invalidated about the previous one for that. So you can still go look at that reference. It, it just makes it way better because now your compute and your storage are segmented,
52:55
right? So over time as we improve on, on the compute side, you'll be able to independently upgrade that. And with ever forever, you you get free controller upgrades. So free a free processor upgrades on a flashlight s every three years with your support renewal. So you know, you can be running on the latest
53:12
and greatest of absolute fastest of what we have to offer. Um So there was one here about and I'm gonna kind of put two together here and maybe this all tossed to you Andy. So question from it says name right about how to prevent active ransomware attacks or Attackers from getting into active directory. And then someone also asking um actually he asked as well about um reaching application
53:36
endpoints. We hit on some of that. But man, there was so much we were covering any other thoughts you want to add in for those two with ad. There's a lot of hardening. I would go through the Microsoft guides. They had a concept in the past called Red and Green Forest. They've been renamed since I in the last couple
53:50
of years, I don't remember what they transitioned to, but, you know, you have basically a, a separate administrative force that you can create, that locks it down to very specific computers. Uh So P CS that have special card readers and cards associated to be able to perform administrative activity.
54:09
It's extreme, but where you do it, you can really make it hard for an attacker. Uh So I highly recommend going out and researching that concept, Red Forest, green Forest. Um And then what the application piece I, I didn't understand Andrew. So, um, if you can help me, you know, it was just about protecting application endpoints.
54:26
Uh the kind of endpoint protection which we, we have lots of companies that we, we've worked with in the past, we don't focus is pure. So anything you want, we're looking to partner in some spaces, right? But, but in point protection is, is uh you know, its own kind of beast. You have to basically,
54:40
you know, for monitoring purposes, wherever you have an application in point, you should be logging that via or elastic or, or, you know, whatever your your uh log logging platform of choice might be logarithm, whatever and make sure you're ingesting those logs into a common big pool of, of warm and hot data because you wanna be able to analyze it very quickly,
55:01
right? So, um, any application end point should have that logging capability in place. Certainly as thing one, but then you need to define a security stack around it as thing too. So, anti malware, that general stuff, but don't expect that's going to stop a ransomware attack. Did I have a request? I'll go ahead and do this from Matt about
55:20
killing the background music during Q and A. I was trying to pull it down, but if that's hard for folks, we'll pull it up at the very end here. Uh But, you know, I appreciate the note. Um Maybe we'll do two or three more here. Andy, if that's all right, we're still all right on time. I think you are.
55:31
Um one, I'm gonna take a run at first. It was actually kind of a cool question from Harold. They have an active cluster set up. So, you know, so synchronous replication with an older array, an M 50 A 70 they're almost full on the M 50 you know, and what can they do? Actually things are in pods.
55:45
So, uh the answer there is actually overall and we want to dig into your specific scenario, please ro out to your peer account team. I know you've got one. We can actually take the M 50 controller upgrade that non disruptively add capacity and then be able to push further into using safe mode, using snapshots, et cetera. Um So that's actually kind of cool where you're
56:01
not, you're not stuck there. And I think the um there was a question from Matt about tabletop exercises and general outlines. II, I want to be a little cautious here because this isn't something that we offer is pure, right? We have a lot of different partners that offer tabletop exercise and sometimes the outlines of
56:19
that is, is their intellectual property, right, kind of thing. Uh Is there anything that you want to kind of just extra details you want to add around tabletop exercises and you know, even, I mean, like Mandy and got bought by Google for 4.7 billion, there's some big names in the space, but over to you, Andy. Yeah, I mean, look, the big thing with,
56:34
with tabletops is not necessarily the technology outcome, right? It's, it's a lot more of the process outcome and the uh you know, the people kind of outcome, right? One of the things that you'll find when you go through a tabletop exercise the first time is you learn a lot about what you haven't thought through, right?
56:51
So a good example, what, you know, you get attacked, it's uh you know, 3 a.m. all of a sudden, you know, you've got to figure out who you're going to, to call because active directory has just been hit, it's taken down, you know, so you're not sending an email to someone, right? You're not sending an email to your CEO saying
57:07
we've been hit by a ransomware attack. You're literally making phone calls. So do you have an up to date phone phone tree that you can call. Do you know who the application owners are for the applications in your environment so you can get a hold of them? Are they up to date or do you have people that haven't been with the company for three years?
57:23
Um Things like, what are you gonna do when Joe or Sally? And it start tweeting about the event, you know, what, what happens, you know, when the media shows up and you've got a hostile reporter outside who, you know, is just being a real jerk about the incident and wants to know what's going on, right? There's a lot of stuff that, you know,
57:40
you have to just think through around how these events could unfold. I think the last one here. Um and it's amazing how many folks usually hang with us. We've still got the vast majority of people hanging out with us. So without the fun music, um maybe I'll, I'll put these together a little bit Andy.
57:57
So and then you can, we can kind of rift together. So uh from Gloria, you know, some questions about average turnaround time for a, you know, a 5000 employee company and you know, helping executives and then John even had some questions about, you know, how much does down the stack matter. I'm gonna go in reverse order the down the stack matters like sequel and o si mean,
58:16
that's the attack vectors that once they get it initially, the Attackers can take advantage of to be able to maybe get into memory and dump back to directory domain admin credentials, that kind of stuff. But let's say they both around kind of turnaround time and where to focus from a hygiene perspective. I mean, turnaround time is hard to measure, right?
58:34
It, it, it really has little to do with the size of the organization, to be honest, it has everything to do with the complexity, right? And so if you have a highly complex organization with, you know, complex applications that have been built, it's gonna take a lot longer to recover than an organization who doesn't have that complexity.
58:51
Uh So, I mean, I think that's thing one, it also depends on how pervasive the attack is, you know, if somebody hits AD DNS and time service all three and, you know, your core, core applications that's gonna take longer to recover in a lot of cases than, you know, somebody that just hits a, a, you know, some downstream database that's not that important, right?
59:09
So the size of the organization doesn't necessarily serve as a huge dependency, you know, the complexity of the application space is what probably does. Um You know, I, I think, yeah, I think I'll leave it at that. So what was the second part of that question? Andrew. It was just about about kind of focus like there's so much to do we can focus the
59:29
application level, we can focus at the os layer network lever. If we're trying, if they're trying to do some prioritization, like there's all these things to patch, what are some principles around kind of prioritizing down the stack? Well, you always start at the outside and work your way in, right? You hard, boil the egg, so to speak,
59:44
right? You wanna have a but, but what you don't want is a raw egg. You don't want some really, you know, nice hard outside shell that then gets penetrated and is complete. Go in the middle, right? So you wanna hard boil the egg, right? And so find a way to make, you know,
59:58
work from the outside in to make your, your environment more secure overall. But you, you know, that said you, you always want to start with your most critical applications in any hygiene program right now. The problem is with almost every organization, your most critical applications are also the ones that are gonna say they can't be patched. So you're gonna have some app owner saying, well, that's our,
01:00:19
that's our most critical application. You can't touch it, right? Well, that's the one you have to touch. So you, you have to find the right ways to put the management program in place. Um I like to talk uh about um some of the capabilities that Avanti has, they have some great patch management uh capabilities that also tie into their risk
01:00:38
management capability. Um So it might be something that's worth going and look, checking out. Uh But you know, something to, to at least keep in mind. Awesome. We'll close with the plug for, please make sure to join us next month. I try to bring interesting guests, interesting topics.
01:00:54
We'll pull the music up just a little bit. Thank you all for staying with us. It's amazing how many people hang out with us even like a minute or two past the hour. I guess y'all don't have other meetings to get to or maybe your, this is your bio break time, but either way, thanks so much for joining us for this month's July Coffee Break with pure storage and Miller
01:01:11
here on behalf of Andy Stone. Thank you, Andy. Wishing you a good day, a good week and a good month. See you again next month. Let's keep it going guys. Keep the conversation coming.