00:00
And we're live. Hey, everybody. I'm Jason Walker. I'm the global practice leader for modern data protection at Pure. And uh that's is Rick Gay. I'm the principal technologist for the Americas at combat. And just in case you think we're lying, there's our names.
00:18
So you can believe everything you see in writing on the screen there. It is right there. I did that. That's good spelled actually if it's in writing you can this segment uh is the modern data protection experience. It sounds like a seventies uh funk band, but that's uh it's only slightly true. Pure Storage and Commonwealth.
00:36
So we alluded to it before most of you are already here. Uh Rick and I have extensive experience. We're doing this for the on demand folks on the uh recording 100%. Absolutely. So, Rick and I have extensive experience at each other's companies. I worked at from 2005 to 2015 and I worked at Pure as the Cloud architect from 2018 to 2020.
01:00
Yeah. Good stuff. So as we switched kind of uh places, Freaky Friday style didn't switch body. So that'd be really too weird. Um you know, we've uh we have a lot of passion for both companies and what, what's possible and passion about data protection passionate about.
01:19
Um Yeah, I mean, really about the world of data protection, not just back up, although you could throw it all into that and then, but data protection as we know is a lot larger than that. So, you know, gee whiz, how did pure storage get wrapped up in back up? Why is pure storage a partner of, of pure Rick? What, what's been going, what was going on?
01:37
How did we get here? Well, you guys all saw the last couple of years, you know, we went from restoring a single VM single file to, oh no, the data center is down. Uh It's an ugly landscape today compared to what it was five years ago. So that, that fact with I I wish pure had the, the old slide around data growth in here. Remember 100 and 75 zeta bytes,
01:58
the hockey stick of data growth. How's your SAS changing? Are they? The data is growing exponentially? But the SL A is the same and that is why. Yeah, that's a, that's a, that's actually it, I mean, it, it seems nostalgic for me to think about uh restore circa 2006, 2007.
02:18
It was uh you know, can I get my email back, you know, to talk about a single email? Not the whole thing. Can I and then, you know, can we get a, a single VM back? But now we're answering questions about how do I restore 100% of my data center or even 50% of my data center. And some of the, the challenges that you see
02:35
here uh are still sadly in play, we think we would have solved, uh you know, the industry would have solved all these by now. But what we're finding is, you know, data, you know, combat data sitting on some targets that are still, you know, slow and they, they're not responding to the demands of that hockey stick that Rick Rick talked about here at all. And, you know,
02:56
and, uh, you know, some of the solutions out there don't have any concept of efficient cloud use out there. Rick, I know that's something obviously very, pretty, pretty close to my heart if you, yeah, if you're, uh, building up in the cloud, which a lot of folks are, you need to make sure that the solution that you're choosing is built to the cloud spec,
03:14
not just an emulation of what's on prem. It's a, that's a, that's a thing because the cloud is, you know, the ethereal, uh, word there. But you, you do really, you could cost yourself a lot of money and spend a lot of time. Yeah, very quickly not being, uh, intentional about what you're trying to do in there.
03:33
And I think a lot of companies race to have a solution in the cloud without thinking about some of those things. Uh The customer Conwell does a great job of being intentional about some of the things. Uh shoot that's been going on for years now with auto shut offs of media agents and things like that, auto scaling, auto scaling, automatic dynamic provisioning.
03:53
So you don't have to manage the boxes. That's right. So you're gonna be surprised we're gonna go from problems two solutions. I know that it's incredible, but this is the things that have definitely come into play. The reason why me a long time backup guy chose to be in storage and and R A storage guy who is now with a backup company we passionate about, about these things,
04:15
but simplicity is, is super important. We heard it all who was in the keynote today who didn't like Shaq, I'm not talking to the LSU guy in the back because I know, I know uh but um who didn't like Shaq before the keynote but came away with without liking him a a little more or who likes Shaq more now, let's say than they did before, right?
04:39
Shaq is so cool on that. I, I really appreciate that. But during the key note, we would, you know, we heard a lot about simplicity and simplicity is still critical on on what what we're doing, the more complex as the previous slide said, the more complex things are the more costly they become on there. So simplicity is still important. Who's ever said?
04:59
Uh, you know what I want, Rick? I, I don't want something faster. I want to go slower. Let's do it. Who says that? Nobody, nobody even in baseball now things are, you know, let's move it, let's speed it up a little bit here.
05:11
Let's get it going. Speed matters. And, and one thing that Rick I've seen is a lot different since coming here. Think it's always been important to me combat, surprising, you know, you might be surprised to know that restore has always been a keynote of COMT Comal was the
05:26
original data control plane to be able to treat disk like disc. And that was critical for restorers because it got away from shoe shining even across disk drives, right? That was a big deal when it comes, came to recovery. That same spirit of innovation that saw combat take, you know, take that random and, and bring it to the to the restored thing is still going
05:50
on today. The innovation still continues and it is rare, I think to see a company that's been around that's publicly held. You know, our stock is traded, usually R and D gets cut to make a bit and we spend more on R and D than most companies out there. Definitely more than almost any other our size. And the reason that we do this is we want to take advantage of things like flash blade.
06:13
When it came to market, we were very fast to adopt the capabilities and give that to our customer. Our software tends to not be the bottleneck but it will find the bottleneck in your environment. And today it's, it's kind of an interesting problem. It used to be that the backup media was too slow.
06:28
Now, it's the opposite coming off a flash blade, we can swamp a couple of primary arrays simultaneously. And uh that's a good place to be when you're trying to recover as much data as quickly as possible. You're limited by the right speed of your primary storage. Who who here thinks who's heard of Flash Blade?
06:45
And there are a few who's got them. Ok? Who thinks Flash blade was built for an old uh backup guy like me for backup workloads. Who thinks that good? Nobody, nobody thinks that Flash blade was not created for the data protection use case created for the sexy, you know, next gen workloads A I which works super well on I I
07:11
mean, if I can give some insider stuff, it, it was actually built for pure to get the data out of AWS for pier one and then it works so well. Uh It became a product to the end user. Yeah. Yeah, not created for me but uh as as time went on and we went from the single file, single email recoveries to large larger scale. Our it's the market that said, hey, you know what, I've got these sexy next gen workload
07:38
flash blades sitting here and they're very good for fast read because that's what you need for those in high parallelism, high parallelism, you know, highly, you know. Gee, you know what another great use case is with high reads restores, right? So our customers kind of brought it, brought it in, uh, brought it into that and the rapid restore use case uh was born,
08:01
was born here. Yep. Yep. It's kind of the same project again. It's, it's one of those things you always hear old. It guys say, oh, it's come full circle but it never is full circle. It's a Helix and it moves forward. I remember my mainframe guys telling me VM Ware wasn't anything new. Well, let's be real.
08:16
The mainframes virtualization compared to what VM Ware can do from an ease of management was night and day different. It had moved forward. And this is kind of like if you guys remember when you replace tape with disc, it, any old disk would do right near line. Sass cheap and deep, give me as much as you can and that was good enough.
08:33
But this is the same project again, modernizing the data set to keep up with the slas with data growth because nearly just can't cut it anymore. Things change. And you guys walk into new slas every day, every day, the expectations change. It's not fair. Well, how many have big data leaks or any? I got one back there.
08:53
A couple. Is it, is your insurance telling you that you have to protect that data now because that's what we're seeing. Uh We've got over 100 petabytes with a major automaker on the table right now and it's all data that back in the day you would have went to probably an isil on 20 years ago and they would have said, oh, you don't need to back that up,
09:10
just replicate it. Well, that's great until it's encrypted. And then the replication is encrypted. So it tends to be a line of business data. So we're actually starting to see where customers are coming to us for tens and even hundreds of petabyte environments that were not backed up in the past. And they want slas on that that are within 24 hours.
09:31
So how do you recover 100 petabytes in 24 hours without blazing speed on the back end it. I've seen it. And, and when I began here in 2019, when we would talk about our rfps on a recovery or any ransomware, not even recovery just on ransomware, prepared preparation or a backup target. We wouldn't see the word restore in there. We, we still didn't see that in 2019.
09:57
And, and one of the reasons is that it's, it's easy to test backup, just make another copy to something. It's harder to test large scale restores because largely the, the only space you have for that kind of restore is in production and you don't want to do that. So it is extremely critical. But what we've seen in the last four years is restore.
10:17
Language has become a part of almost every RRP. It's a part of everybody's planning, application validation, recovery validation. We've, we've automated it in the platform so that you can actually recover a piece of an app or the whole thing or a multi tiered environment. You could have it, run the DR program for you, isolate it,
10:38
run it once a month with zero touch from it, spin it up, scan it, make sure all the services start, shut it down, send a report to the compliance team. You don't have to sweat it. So we're, we're seeing that we certainly, when we consult with,
10:50
with customers at the big picture, you know, stuff that it doesn't even have to do anything really with pure. Those are the types of things you say, hey, whoever you choose, make sure you're planning on restore testing. And we just had a, a guest, a customer in the previous session that said the same thing, they test 150 VM restores uh every month or something like it was every month or every most
11:11
or every month or quarterly. It was just incredible. But that is, that's the right thing to do. They, they test it by restoring into the cloud. But if we're doing snapshot replication over to Dr is where most folks on that. So if we're replicating flash array snaps to the DR flash array and then we do the restore there, guess how much capacity it uses.
11:29
And then the operational agility of subscription, uh you know, with, with pure uh the one of the saddest things I see all the time is uh talking to customers who here's, here's all the goodness and want to take advantage. We just can't because they're locked into two years or something and you just see the color drain out of their face and, and that, you know, the evergreen subscription,
11:50
you know, you know, means being able to be more flexible as these slas are changing um every day. So here's a loaded question, you know, Rick uh why, why pure storage and combat? What makes uh the, the two of us so good to together. So I'm gonna kind of fluff flash blade a little bit.
12:10
But, you know, you guys can remember S3 came out in public cloud space, it was globally available name spaces with high parallel access. They were unlimited. Uh As far as our knowledge for the most part, as long as you brought your wallet. At the same time, people tried to emulate that on Prem and it just didn't go well there.
12:28
I had a lot of people tell me, 0 S3 on Prem is terrible. It just doesn't work. And then Flash Blade came to the market and it kind of changed the game and we had done a lot of development with Amazon on their S3 platform as a target. And we wrote a piece of software, a snippet called storage Accelerator. It was cloud accelerator at the time.
12:47
And what it meant was instead of bottlenecking everything through a set of media agents to do the D do, we would do source side d doop and write those sessions directly down to the S3 storage. So you'd have thousands of sessions streaming into S3 with flash blade. We can bring that cloud like experience onto Prem and understand that those are
13:05
bidirectional streams. So if you've got 1000 V MS to back up every night, we can stream 1000 different sessions to the flash blade. If you had to restore them, it'd be 1000 sessions right back in. And basically we chase that bottle neck out of the back end of the storage.
13:20
Yeah, it's uh and that speaks to, you know, the, the leadership of when I came on when I came on board combat was unfairly being lumped even by people at pure as being legacy. And maybe you think that today. Uh and I can understand why because they, they're experienced, you know, they've been, they've been around and it takes time to build a legacy,
13:39
doesn't it? But is as Richard was just talking about t has always continued to innovate what he just described. Not many other folks have uh in the data control playing business, certainly doesn't do it as efficiently as Comal does. And you know, even Comal even stopped to rewrite how they wrote to object
13:59
libraries and innovated in that way, creating these TCP birds that honestly were a perfect fit for flash blade because here's flash blade sitting waiting for a huge distributed workload to fully take advantage of it. And the way that writes the object fits uh just perfect. So are leaders and still, you know, Gartner leaders today, 11 out of 11 years in the magic of the first day when it first
14:21
crossed over and then they haven't stopped since I thought when I left, it would break the street. But, you know, it didn't, it didn't kept soldering on the products, just that good that they could uh do that. And they've stayed modern in being able to do it, Rick. You know, we, when we talk about modernization, first of all,
14:37
writing the object is something that a lot of other data control points. If you're not using combat today, you may be with a data control point that really doesn't understand how to write efficiently the object and make the most of it treating it like a long term archive storage, almost like writing it to tape frankly, you know, from a, from a, that's the thing. There's a lot of me too out there.
14:56
You'll hear other competitions say, yeah, we can write to three. But in order to do that recovery, it's got to go back into their proprietary file system to be rehydrated. And all the speed of the flash blade then is only beneficial up to those bricks, which isn't your restore. So you're still bound by the brick speed. And we see that we see that a ton in the
15:15
industry, there's a lot of, you know, we look at it as uh imitation is the best form of flattery. So, you know, we're happy we'll golf, clap them for developing things for S3. But let's take it to the next level and what's gonna be S3 version two and I bet we support it before anybody else does. Absolutely. And what Comal innovates, uh you know,
15:33
Rick from a security standpoint and what's been going on and on that side with you guys has, uh you know, it's, it's all who knows that it's all hands on deck when it comes to ransomware, right? Everybody pitches in pure, has something to pitch in and, and has always had a good set of tools, but it's taken even to another level. So I'm gonna go ahead and throw this out. Is anybody in here pretty confident of what
15:56
Comal does from a security perspective? I mean, there's a lot of noise in the industry. Um Has anybody heard a whole bunch around comb security? Right. Our marketing CMO just got replaced. Uh and the, yeah, we'll just say that a lot of the security features,
16:14
you know, we've done multi tenancy for over a decade. What does that mean to you? That means role based access control, multi per person authorization. Those kind of things have been baked in for a decade. We probably shouted about it back then, but we haven't been good at bringing that story back into being relevant.
16:30
But beyond that, we're one of the only if not the only solution that has proactive threat detection, meaning we don't catch it after we backed it up and scan, we do it on the front end. In real time. We have deception capability, meaning you can spoof entire environments iot we have the ability to do behavioral analysis without being cloud connected.
16:51
Your behavior does not come into our cloud. We're the only solution that's federal ramp high, others are pursuing federal a moderate and we're aisle four and aisle six, if you know what that means. So three letter agencies love us and have four decades. So we're used to the attacks, the style of attack that's happening to the non government
17:10
entities today. Meaning, you know, we've got foreign actors, state level threat that's not new for us. It's probably new for a lot of you. But these are environments that we've protected for a long time and we have a hefty amount of experience including former NSA employees that are in our staff that help with incident response that help with recoveries. We do have a ransom recovery team and just know
17:36
that if you are hit, our executives are alerted first, our entire c suite gets notification that we have a customer that's suffering an issue and we have a dedicated response team. Now. Pure. You wanna talk about what pier is doing? So I was just gonna say that doesn't sound like a legacy. Sit on your hands 11 out of 11.
17:55
Uh we're leading in the space just see some things this year type stuff, definitely still innovating and that's why is still is, is engaged so much with that because Pura, as you heard, you know, earlier in the keynote is dedicated to, you know, obviously some of the, some of the obvious ones here being performant,
18:13
being simple but being secure sustainable and has been a great partner of that and, and, and we, I get questions all the time, you know, that, that folks that are customers and are very aware of what you guys do from security, very worried that we're gonna screw it up. We gonna send this data to Flash Blade and uh you guys just gonna,
18:33
you're gonna be because you're only strong as your weakest link, right? So uh in, in there, they're gonna, you're gonna be the weakest link. I mean, I heard Walker talk and now I'm really concerned they're not saying, yeah, they're not. So it's actually harder to go after data. That's protected with com vats, worm and compliance lock on flash blade with their safe
18:53
mode. It's harder to go after the backup data than it is your production data. I'll tell you that. Yeah, it, it fits together. It's, it's a combined approach. So, no, it would actually do it with object lock now available. It's toggle, turn on the worm lock inside a com vat.
19:07
It will initiate an API call to the blades and tell them to lock the data for the retention set that you've set and, and then you can, you can use uh what the what's called unfortunately, uh safe mode retention lock on the bucket itself for denial to protect against denial service and eradicating the bucket and things of that nature just layers upon layers of goodness. So who's, you know, I mean, I assume everybody
19:31
in here is asked about keeping data secure or is concerned with keeping data secure. So that, that definitely the more critical pieces. So you can hear, you know, the, you know, the leaders that we are in the spaces and modern solutions to modern problems. But keeping it simple.
19:47
And uh certainly folks that have chosen to, you know what I say, supercharge combo giving it, you know, restore boost and everything. But we do it in a very simple manner because the object object is simple, you set up a single bucket as a cloud library, uh doesn't get easier and just expands automatically and we're, we're in, in cahoots right now trying to actually make that even
20:08
simpler. Where if you have a flash blade inside of Comal, there will be a drop down that says flash blade and you can do a create bucket, give it a bucket name right inside a con vault. It's gonna send the API calls. Uh So that is road map. It's on the product today, but it will be there probably this year. Uh calendar,
20:27
another flash. How does that play? It's a, it's a great question. So we're, we're aware of the retention set and what we do is we'll seal our D DB. I don't know that you guys know that we embed all the metadata that's in the D DB gets embedded in the backup job. So you can wipe the entire con vault environment off the map.
20:49
D doop is not used for restore. So we don't have to read back the D doop database that's only for additional data coming in. And when we lock that, we seal the D DB and we lock it on the storage at the same time. So that entire metadata intact set is completely untouchable. At that point, we start a new, new set at that point.
21:09
So there is a, a capacity bloat that you will get with locking. Um If you are landing on flash array instead of flash blade because of the, there is no bloat. So keep that in mind, we, we call it that, but it is a solution because what you get from that is as soon as the dot Job is finished, it's locked, it's locked,
21:29
it's immutable on land. It's immutable on land and it's instant thing when you go to do a restore, uh, we're not rolling anything back where there's no that you're, it's just, it's ready to roll if you had a combat for those combat customers in here. If you lost your serv database, if you had to rebuild and you're doing a true disaster, once the S DB is loaded, you're ready to restore because we're,
21:50
we're still protected. We still have that data protected in there. That, so the thing I was gonna bring up when I asked you to talk about what peer is doing. Can you talk about that ransomware recovery subscription? Oh, yeah. Well, it's a part of our evergreen one, package. And what, what it'll do is, is, uh, it will
22:06
actually guarantee that you'll, you'll have a clean array and be able to get data back within a certain sl a period. That's, that's what I was talking about. So, one thing that people maybe don't know is that if you are compromised, a lot of times when you engage law enforcement, they will prevent your recovery, you will not be, they will have this question, they will block your array in its place so that
22:28
they can do a forensics audit. And if that's your primary storage, if you don't have another location to recover to, you're waiting on the feds, the locals, who knows. Um, but with peers, with peers equipment on Prem again in 48 hours, I think is one of the slas you can get, I'm sure they're gonna have different things so I
22:48
won't speak for them. But if you can get new gear on the site immediately with everybody, I love it. It's, uh, that's a, that's a very unique offering in the industry this year. I just had that question. What if the FBI comes in and say, well, they could, you know, and uh and they do copy it to another way.
23:02
There's, there's uh solutions around that for sure. That's it. Uh Who who remembers me saying is flash blade created for was flash blade created for data protection? The answer was a resounding no, but the market drew us into it. And uh our classic flash blade was so popular and, and then working with combat became such a
23:23
popular uh solution that customers, your c our customers insisted on more, more options, more into that, you know, hey, I do great. But I want luck, you know, and uh so now we have a whole family here to choose from. Now, I know choices uh makes things seem more complex but really every, everyone, everything aligns to the single outcome that you already have in mind.
23:49
So, you know, let, let pure, let com vat help you decide what that is on there. But just know that there's a lot of options available based on the outcomes that you're looking for. I mean, ultimately it comes down to your objectives. The nice thing is that COMT is so tunable and with a with a bigger portfolio, you have more options, price to performance options,
24:09
things like that capacity, you know, per dollar that really allows us to help you tailor your suit and that's what we want. You know, there are other companies out there with appliances and yeah, we have appliances too. But if all I have is a box, how much do your outcomes matter to me?
24:29
I'm just listening for back end terabytes. That's all I have to do a size for. Oh, it's gonna be two petabytes on disk, right? That's as many boxes doesn't like to operate that way. So it is a little bit more irritating probably to deal with us because we're gonna ask you about your network. We're gonna ask you about your storage. We're gonna ask some more questions.
24:44
We're gonna have a lot more discovery and we're trying to fine tune what your outcome is that we're actually having to achieve to make sure that you're a happy customer. And that's, I think that is differentiated versus just pushing boxes. That's, that's the approach to take because you want to provide the most, you know, the more detail and the more specific that the outcome looking for is the better the
25:08
picture you can ask me, uh, to draw a picture of a city and, you know, I could get it done with a couple of, uh, poorly drawn houses and, uh, you know, thing and maybe, uh, an attempt at a stop sign with the shape is not quite right. But, uh, when you take the time and ask more questions about what, what's in the town, is there?
25:26
How many people live there? A more full picture on, on that as well. All right, poor analogies aside. Let's uh let's move on. Uh You know, we talk about recovery. Uh like I say, you, we obviously flashback fully tested object lock.
25:40
This is your highest performing target in there. And when I say highest performing, I mean, restore time target very fast speeds. Uh you know, up to, you know, anywhere between 70 100 terabytes an hour recovery. That sounds pretty good. Sounds good to me. I don't know, but I, I work here.
25:59
So we actually, we actually exceed that with some designs, we exceed that with some designs in flash two petabytes per hour is, I mean, it, it really just comes down to how much data do you have and what can your network do? What can your primary storage do? How much, how, what your source is to, to restore to?
26:16
But that's when you're talking about recovering 100% of your data center. That's the kind of speed are you talking about? I don't have three weeks anymore to get back up from what does it cost you to be down for three weeks? Right. I mean, one thing to note is that com has got over 100,000 clients and we have a ransomware incident or a cyber security incident with a customer 1.2 times per day.
26:40
You haven't heard about 470 of our customers last year getting hit. And that's because of the proactive capabilities and the ability for us to identify blast radius and point of impact and get them back very, very rapidly with the technology at hand. So they don't make the news and we don't want them to and,
26:57
and we remember that flash plate is a multipurpose, it's multi use multidimensional, uh use it all day long as a great backup target, but that doesn't prevent you from using it for those sexy next gen workloads. Uh If, if you want to, I mean, if you want to go beyond data protection, I suppose you can and doing that and doing it in a footprint of uh you know, to makes it a more sustainable,
27:17
you know, energy wise uh as well and, and of course, the security is there by maintaining uh object lock there. Um Yeah, we talked about the immutability here and, and what you're, what you're getting for uh you know, stores and, you know, Rick and I have talked about that you, the, the goal is the fastest recovery possible.
27:40
So that's what it's in place for. And you might, you there are solutions out there that will have no problem telling you that you need three sites dedicated specifically to be able to deliver what you can get in one flash blade in terms of the protection and the immediate recover. And remember, you know, Rick, I talk about this all the time but has a,
28:02
I think the, I think the scientific measurement is called crap ton of uh of function in the software. You're familiar with that term. Uh And uh you know, but a lot of those things depend on read to be highly successful. Absolutely. Yeah, we anything from, you know, discovery compliance searches, pi I searches, all of those things are gonna read that data.
28:25
So the faster we do um off of that back end storage, the faster we can get through those indexes and give you the the data sensitivity scores and you know, scanning for threats. Now we do a post process antivirus scanning. There's all kinds of different things that you can do with that data, even refreshing environments. You know, we do a lot of uh digital
28:45
transformation where you might have some stuff that's running on prem and sequel on an always on cluster. We might want to recover that off to the DR site with data masking. And we do those kind of things pretty rapidly, especially when we're back with something like flash blade. Yeah, uh even secondary copies.
29:02
I always, I always say that, you know, in the very beginning when we started doing this, had a customer that contacted us. Uh we were following up, we wanted to know how the performance was. They got back to us and said performance is great. You know, talking about the kind of speeds and simplicity at scale that they were getting from
29:17
object and, and con vault and they were just very happy. They get the most out of the comb software. But they said, uh you know, they were going directly from uh on prem to tape. Tape was their next stop in the backup tour which manages the thing I like about is doesn't matter what you're reading from or writing to,
29:36
it's just totally intelligent, but Rick, it was so funny they were going to tape and they called, they were very excited. Now, we, we would never put this on the brochure, right? Uh or at the front of the website. But they, they were so excited that their tape copies, copies were faster and they said we could even, we can keep the tape library heads busier faster now because we're on the head
29:55
because you can read the speeds in there. It's a very nerdy thing to be excited about, but I was excited with them, Rick. Uh But that's uh that's what you get. Uh you know, in that combination. And as we talked about uh safe mode everywhere. Now, we've talked a lot about pure as a target, pure as a target for vat Comal
30:14
writing to pure as a repository. But I think the most exciting stuff comes with pure as a source uh in there, see, not just about restore, although it still is kind of uh it's all about, you know, the restore, the fastest way to restore is snapshot, right? They do snapshot. And one of the things that Cobalt has totally
30:38
pioneered and is still best in the industry. Bar, none is independent snap management. The ability to work with a storage platform to orchestrate snapshots, be able to mount it, mount those snaps and get index granularity so that you have all your restore options that you would normally have without even having and then back up and back
31:03
up. So incredibly intelligent talk about. Yeah. In Yeah. So Intesa is actually free. It's part of the product. Um It's been part of the product for a long time. It's free, it's built in, it sounds like pure. Yeah. And uh so the inte feature, what it does is it
31:18
leverages the API S of the array. So it's not our API S, we're actually calling purity. We're using rest commands to tell it to orchestrate snapshots. And we can use that in a bunch of different ways. The most common is for VM Ware. And yes, it supports Vival.
31:32
And yes, we're the only one that can restore it as a Vival. But what we do is we'll tell vmware to take a snap. We'll tell the P A to take a snap. Then we'll let VMWARE release its snaps. This avoids stun. It keeps the worker snapshots happy. Very small.
31:48
Once we've got that snap on pure as you know, um you can't mount a pure snapshot clone to a volume. That's another command that we send clone to a volume and mount it over fiber channel to one of our boxes where we actually can read through. Now, it is vmfs or Vival or what application a sequel oracle doesn't matter to us. But we have the ability to integrate with all those apps for years and years.
32:09
And that experience, that legacy means we understand what a vmfs volume reads like or what our man backups read like. So we can actually pull those natively get you your item attribute level backups and then you can decide, do I want to keep maybe a couple of days on the array of snaps? And now there's safe mode for those as well. So you could lock those snaps.
32:31
We do name them differently in, in purity so that you can tell this is a combat created or managed snap versus one that was users. Yeah. So um and then we have the ability to trigger replication now, so you can take that snap from AAA and we can replicate and manage the replica over AD R, which also means that if you had to do AD R recovery, we can initiate that in our run book from the DRR A which is,
32:54
it's rare that any, I mean, there's some that do snap integration, but I don't think they do it to the level that, that we've built as a global practice leader. I work with, with everybody and I love all of our partners, but is the only one that can get to this level where you can have uh control plan awareness of the of the AYC replication or even an active cluster pod and then even an AYC replication
33:17
off the back of that active cluster pod, three site combat, aware of all of it and can take action at that third site as if they backed it up at the, at the first site, love active cluster. Personally. Do you guys know that if uh if you've got active cluster and a third site is taken a replica, it doesn't matter what each side of that cluster is up,
33:35
it will always make it to that third site. I always thought, oh, it's gonna come from one array or another it has to pass. So, you know, you go to Philly and then it's gotta go through Philly before you can get whoever's closest gets it. So it's pretty cool. You will guarantee an sl a to your offsite, even if one side of the clusters down.
33:51
Absolutely incredible. And, and folks ask me, folks, folks who's familiar with pure snapshots here, right. Uh It's, they're great to use, easy to use. I've had folks ask me all the time, why would I even bother using combat? I mean, Rick Cody gave you a lot of things. Why?
34:05
But it's all about adding resiliency tiers to your plan. Uh Backup is great, but it's a last line of defense and, and you've got applications and you've got workloads that were, that were gonna require differing levels of support. And this is great. You could do that with pure.
34:22
It's even better having the granularity and orchestration of combat doing that with within telesp difference. We do some crazy stuff around database too. If you consider that a Flash blade can do NFS and S3. So let's say you've got sequel and you guys like to do log dumps, give them a mount on NFS on the flash blade and we can sweep that right to the S3 on the same
34:43
flash blade. So you're not eating a volume off your sand. You know, it's, there's all kinds of incredible there. Again, what are the outcomes you're looking for? Right? And it's very easy to, to, to map that map that in uh map that in there. All right. And Rick, yeah, that's another thing.
34:59
So Rick, you're the cloud. We, we're contractually obligated to let Rick talk about a lot of cloud uh on here contractually, I didn't see the CBS, but now we've talked about, you talked about in Telesp and what it can do and pure has this cloud block sort thing. Rick tell talk about it. We know what, what the possible is around some of the outcomes we see there.
35:20
Yeah. So as you guys know, pure runs on purity, that's the operating system. So if that operating system exists in public cloud and it's addressable like an array, which is what cloud block store is. That emulation can take those snaps that can be used for recovery. And the bane of that has always been that the cloud providers will not allow you to boot from
35:37
third party storage and this is considered third party. So if you've got on Prem VMS and you replicate that snap up there, you can't mount the C drive. So what do you do? Well, combo can split the back up, we can run scripts, post process so that you can have an on prem VM on, on vals.
35:54
Those can be replicating to CBS club block store from pure up in the cloud. And then when we do a run book fail over, we can tell it convert from a VM ware VM to an Azure or an EC2 or a GCP project, whatever you want. We do those digital transformations on the fly or we can do them in advance and keep them synced. There's four different ways of SL A there.
36:15
But the slowest one is just doing a conversion on recovery. And when I say slow 400 V MS and Azure takes about 10 minutes and that's converting it from a native format on VM Ware to an Azure managed machine with AC drive that then points to all the other volumes running as Vival is back on the ray mounted on ice. So it really opens up the ability for you guys to do C I CD pipeline using cloud,
36:39
being able to shift that data back and forth, keeping it in a de duped compressed encrypted state throughout its life cycle. So that it's very efficient, minimizes the fees in and out if you have fees and everybody talks about egress. Anybody sick of that. I'm I'm sick of it. Half our customers don't have egress anymore.
36:56
They got dark fiber right into the cloud provider or they're in a and they're on cloud mesh. Egress is the thing that you choose to pay, in my opinion, that might offend some of you. I apologize, but you can have a life without mercy. You can have a life without egress and that really allows you to do what peer did with flash blade on pier one,
37:13
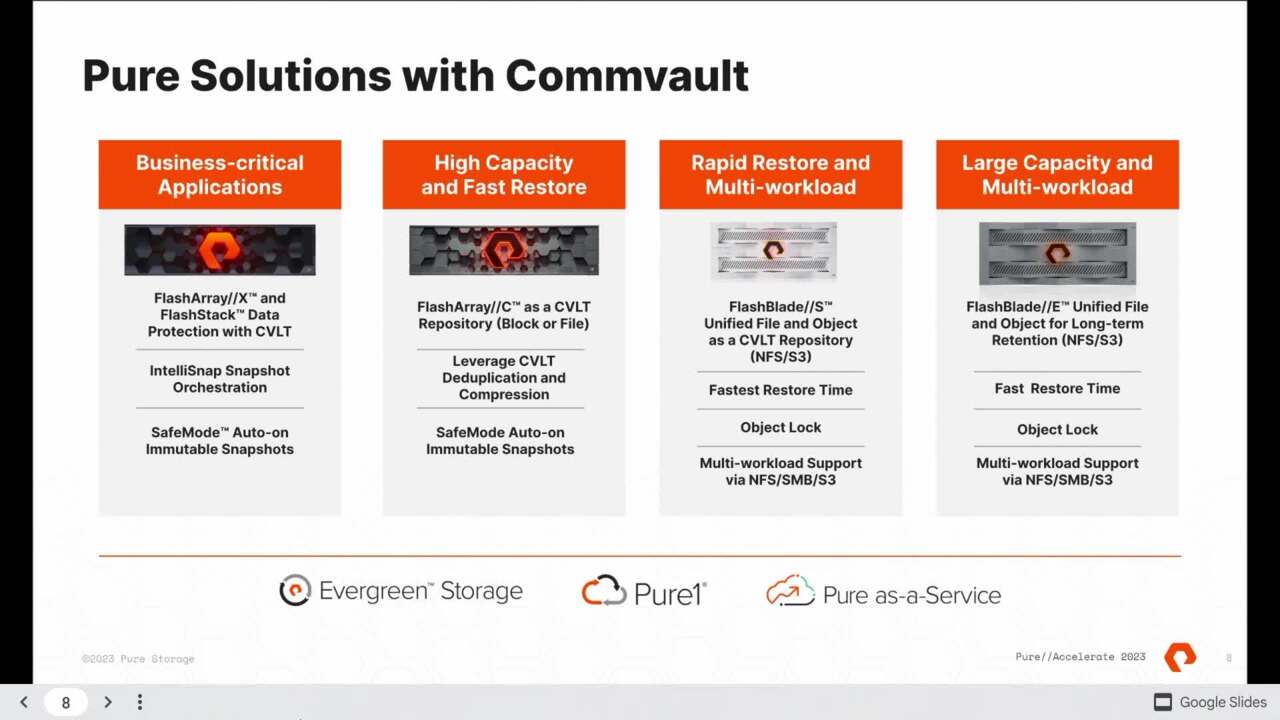
all the, all the processing is still in Aws, but the back end data is not. So two milliseconds true hybrid application stacks, you can do some really crazy things nowadays, you know, the possibilities are really endless uh with that. They're modern. All right. I think this is the scorecard slide to see how we did.
37:33
Uh Talking Rick on there. Uh Leaders didn't have a box under that. So I guess they just assume we're awesome and uh they're right. Correct. Uh You know, modern, we're talking about modern more club. You heard Rick talk about a lot of modern things that we don't necessarily talk on a first conversation about and data protection.
37:51
But it's, it's tomorrow's conversation today. I mean, really be talking talking a lot about, you know, object as a, as a primary target, how to do the, how to do ransomware, how to do it smart, all the security stuff that combat brings to the table and the work with the with snapshot and Telesp adding resiliency tiers is just a critical piece of what you need to do,
38:11
moving layers in a shield. Right. Absolutely. Uh You know, simplicity and we keep it real. It's all simple. I mean, the integration of having combat work with it with it on Telesp uh is real, real easy. Step one, uh you know, set up the arrays in combat, step two, comal orchestrates everything, create a plan,
38:31
step three, go back it up. Exactly. Um You know, it's in the integration uh you know, is there, it's a great marriage of uh it appears a source appear as a target and comb working across the entirety of that, of that rpo RT O Continuum. Uh And both of us, both of us have an open API for those of you that are doing uh
38:53
infrastructure as code or code first. We have API dot com dot com and there's api dot pure storage dot com. And you can see that all of the commands and functions and capabilities from both platforms are open on ours. There's a drop down for whatever your preferred language is. So if you want Terraform go or you want Java or
39:11
Python Ruby on rails C# we've got all those drop downs, consume the code at your leisure. There's also a workflow orchestrator built into the command center that allows you to visually build work flows with code snips to do pretty advanced things. And since you can orchestrate the pure arrays through their swagger and rest API S, it really gives you a powerful dynamic solution to build
39:36
the data center of tomorrow or a true hybrid application stack. And we talked about performance. And um you know, obviously we, we're all about performance combat enables our performance in a lot of ways and we enable, we enable and supercharge theirs as well. And there's a tons, we threw a lot at you. OK?
39:58
And frankly, it was kind of an advanced uh uh overview if we could call something, an overview. It was an advanced overview of, of what the capabilities are. There's a ton of documentation on the Comal site on, on the pure storage site with combat, pure storage slash combat.
40:16
Uh, lots of information there to, to follow up on, there's a combat kiosk. Yep. Uh, in the zone in the zone, not to mention. Um, yeah, I mean, most of your engineers, uh, are pretty familiar with pure. If, if you feel like you need to go deeper on this, uh, you can hit either one of us. Um, we're easy to find on linkedin.
40:39
I'm nature Boy at com dot com. I mean, I was nature boy at pure. I, I like to keep that one and I'm the unfortunately, first two letters of my first name and last name. I don't know. Have I alias when it came to email, they'll make an alias addresses there. But uh all right. Well, uh that, that we'll open it up for Q and
40:57
A but first I wanna thank Rick Gay from Com Vat for joining me up here. Thank you for having us.